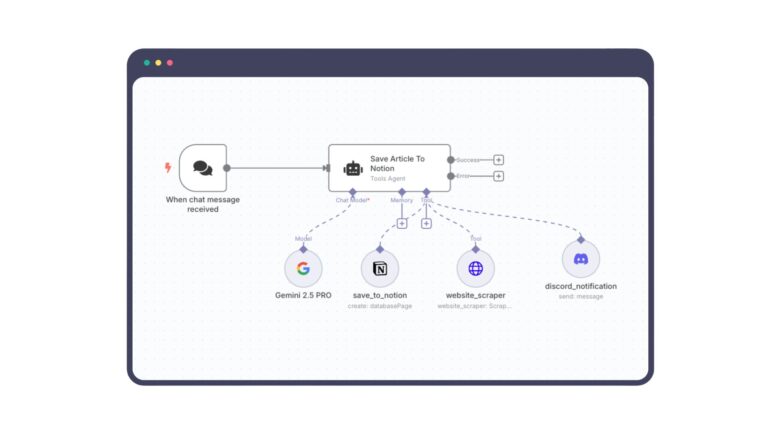
Every now and then, a term sneaks into the AI conversation that sounds both mysterious and urgent. “Agentic AI” is…
Year: 2025
Rising Threat of Deepfakes
There was a time when disinformation took months to plan, millions to fund, and entire institutions to execute. Today, all…
Demystifying the EU AI Act’s Red Lines
In July 2024, the European Union passed the world’s first standalone law to govern Artificial Intelligence. If GDPR was the…
The Old Security Playbook is Dead
Let’s stop pretending traditional security controls can handle AI. Firewalls won’t fix biased models. Encryption doesn’t explain why your chatbot…
Fast AI, Slow Governance. That’s Your Risk.
Everywhere you look, AI is shipping. Founders are racing to market with LLM features. Product teams are embedding copilots in…
AI Security 101: Risks Behind the Magic
Have you ever watched a magician pull a rabbit out of a hat and thought, “How did they do that?”…
How Data Shapes AI’s Decision-Making
We trust AI systems more than we’d like to admit. They drive our cars, diagnose diseases, recommend bail in courts,…
Why Privacy Laws Fall Short in Governing AI
A financial institution uses an AI system to assess loan eligibility. A qualified applicant is denied credit. The reason? A…
Inside the Attack Surface of Generative AI
A deadline looms. An overworked employee turns to a popular AI chatbot to help write code or summarize a client…
AI Governance – I’ve Seen Firewalls, This Is a Forest Fire.
Back in the day, my biggest headache was someone plugging an unauthorized router under their desk. Today, my headache wears…